Do not publish your phone number on your public profile on social media. You can also check for a redirection in your call logs.
 Warning Protect Your Mobile Phone Numbers From Being Hijacked Ccts
Warning Protect Your Mobile Phone Numbers From Being Hijacked Ccts
Ad Top Rated B2B Companies are Hiring Fresher and Senior - 1200 Openings.

Hijacked phone number. But you must secure that. Briefly while this service assigns unique NetNumber IDs NNIDs to service providers for identification swapping these IDs is also possible. Sometimes the purpose of the call is just to check that your phone number is a real one.
Instead they go through your cell phone carrier and that carriers online store. Be discreet about mentioning cryptocurrency on. The fraudsters aim is to take control of your number by convincing your network to either.
If they manage to confirm that it is they may start using it as their cover ID to hide behind. Ad Top Rated B2B Companies are Hiring Fresher and Senior - 1200 Openings. Swap your number to a new Sim card on the same network perhaps by claiming that their phone is lost or move your number to another network by requesting the Porting Authorisation Code PAC.
It is not much different in the mobile phone tracker software also known as cell phone locator or cell phone spy software available on the market. In this appraisal you can explore the best mobile hacking application that is available. Malware embedded in links can secretly download on your device.
You should see the 10 digit phone number where your calls and messages are being forwarded. When in doubt open a browser and type in the address you wish to visit. This attack is also known as SIM hijacking as it moves your phone number from your current SIM card to the attackers SIM card.
If your phone is forwarding to another number it will display after you enter the 62 code. Fraudsters have figured out how to break in to online accounts protected by two-factor authentication where the authenticating device is your mobile. They just plug in the area code and start calling.
They dont need to each into your pocket at a shopping mall or steal directly. Just having ones phone number is sufficient for hacking the phone. Someone with your personal information pretends to be you asking your cellular carrier to move your phone number to a new phone.
The threat model assumed that the attacker would only know the victims name and phone number and that they would hijack the number by purchasing a. This scam has a lot in common with identity theft. Do not click on suspicious links.
Phone hijacking can also happen via phishing attacks. Mobile and landline telephone numbers are being hijacked by phone scammers and it is taking a toll particularly on some victims in regional and rural Australia. Find Latest B2b Agencies Job Vacancies In London On Receptix.
T-Mobile recommends that its customers dial 611 from their T-Mobile phones or 1-800-937-8997 from any other phone to set up an account-protection PIN. Phone number hijacking is a new way for thieves to steal cell phones from you. The hacker tricked a Verizon employee into rerouting Boogie2988s phone number to the hackers phone which allowed the hacker to take control of Boogie2988s email YouTube social media.
Find Latest B2b Agencies Job Vacancies In London On Receptix. That way if your regular phone number is hijacked the hacker cant get into any of these accounts and reset the password. But phone numbers can be hijacked and a recent wave of phone-based identity theft raises concerns that wireless carriers are.
Secure websites send key codes by text message. How To Keep Your Phone Number From Being Hijacked Outsource 630 701-3393 How To Keep Your Phone Number From Being Hijacked This scam can be financially devastating to its victims but there are several steps you can take to prevent the scam from happening in the first place. Thus it becomes possible for an adversary to hijack a phone number without giving a hint to the victim.
While Sim-swap fraud is not new Action Fraud reports suggest. Often they will have found your number simply by using a random number generator combined with an autodialer. How Does a Port Out Scam Work.
And this procedure involves no authentication by the SMS number owner. Hacker cannot ever hack into your phone even though if a hacker knows your cell number.
 How To Avoid Mobile Phone Number Hijacking Best Reviews
How To Avoid Mobile Phone Number Hijacking Best Reviews
 Here S How Phone Number Can Destroy Your Whole Life
Here S How Phone Number Can Destroy Your Whole Life
How Sim Card Hijacking Works Security Boulevard
 How Hackers Are Hijacking Your Cellphone Account
How Hackers Are Hijacking Your Cellphone Account
 The Hackers Who Can Hijack Your Sim Card Using Only Your Phone Number
The Hackers Who Can Hijack Your Sim Card Using Only Your Phone Number
 Hijacked Phone Number How Hackers Access Your Data Social Catfish
Hijacked Phone Number How Hackers Access Your Data Social Catfish
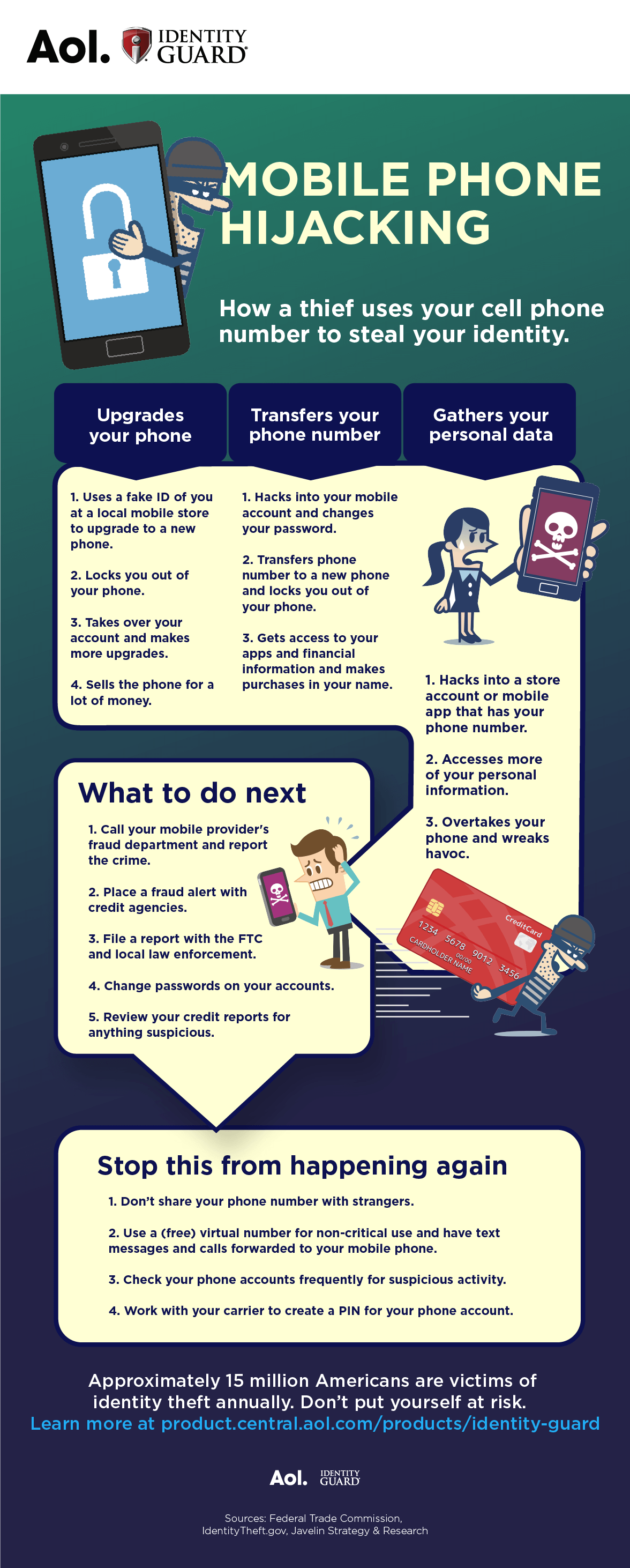 Did You Know Your Mobile Phone Can Be Hijacked
Did You Know Your Mobile Phone Can Be Hijacked
 Telcos Must Pull Their Weight Govt Launches New Crackdown On Mobile Phone Number Scams Channelnews
Telcos Must Pull Their Weight Govt Launches New Crackdown On Mobile Phone Number Scams Channelnews
 Hackers Are Hijacking Whatsapp Accounts By Tricking Users Into Sending Verification Codes Digital News Asiaone
Hackers Are Hijacking Whatsapp Accounts By Tricking Users Into Sending Verification Codes Digital News Asiaone
 How Hackers Are Hijacking Your Cellphone Account
How Hackers Are Hijacking Your Cellphone Account
 Ghost Telephonist Attack Exploits 4g Lte Flaw To Hijack Phone Numbers
Ghost Telephonist Attack Exploits 4g Lte Flaw To Hijack Phone Numbers
 Fraud Alert Id Thieves Hijack Mobile Phone Accounts
Fraud Alert Id Thieves Hijack Mobile Phone Accounts
 How To Keep Your Phone Number From Being Hijacked Outsource
How To Keep Your Phone Number From Being Hijacked Outsource
 Cybersecurity 101 How To Protect Your Cell Phone Number And Why You Should Care Techcrunch
Cybersecurity 101 How To Protect Your Cell Phone Number And Why You Should Care Techcrunch

No comments:
Post a Comment
Note: Only a member of this blog may post a comment.